Best practices for storing and creating.

Weedezign / Getty Images
Today’s Best Tech Deals
Picked by PCWorld’s Editors
Top Deals On Great Products
Picked by Techconnect’s Editors
Show More
Picking the perfect password comes down to a battle between two competing priorities: creating safe passwords that are lengthy and unique, and creating ones you can remember. You might think to yourself, I already have more passwords than I need! I’ve created passwords for years! But with the rise of password breaches, and with more passwords exposed that are linked to usernames, a solid password strategy is becoming more essential every day.
We’ll start out with the basics: the best ways to store passwords, and how to avoid using popular, easily-guessed passwords. Next we’ll dive into the fun stuff: strategies to pick complex, memorable passwords that have a good chance of surviving a password breach so you have time to change it.
PCWorld’s previous password coverage includes:
- How to tell if your password has been stolen
- The best free password managers
- The best password managers, free and paid
- How to create strong passwords by learning how to crack them
- Mastering your password manager: 5 great tips
How to store your password
Why remember a password when you can store it? You can already keep passwords for free in major web browsers and Microsoft Edge. It’s easy and even tempting to go this route, especially when the browser sees you entering passwords and invites you to save them.
 Google
GoogleWhether it’s a dedicated password manager like Dashlane, or a password manager that’s stored in your browser—either way, it’s often more convenient to let a third-party service manage your credentials.
My colleague Brad Chacos, on the other hand, argues that a password manager is better. I’ll acknowledge this: Password managers are the more powerful tool—they store your passwords in an encrypted vault, and the best password managers will also work across your PC and phone. That’s why we warned you when LastPass changed its free tier to allow just one type of device.
Password managers and browsers still need one master password that unlocks the passwords stored within. (Microsoft uses your Windows password to store passwords within Edge, while Google uses the password you’ve associated with Gmail.) Even if you have just that one password, it needs to be a good one.
How vulnerable is my password?
You’d be amazed at how quickly simple passwords can be cracked…as well as the months and years it can take to crack more complex ones. Breaches expose these passwords in hashed form; anyone with access can to try and guess your password, using computer power to try billions of guesses per second. As the chart below (developed by professional password-cracking company Terahash) shows, you’ll need at least ten characters in your password to make it secure, and longer is always better.
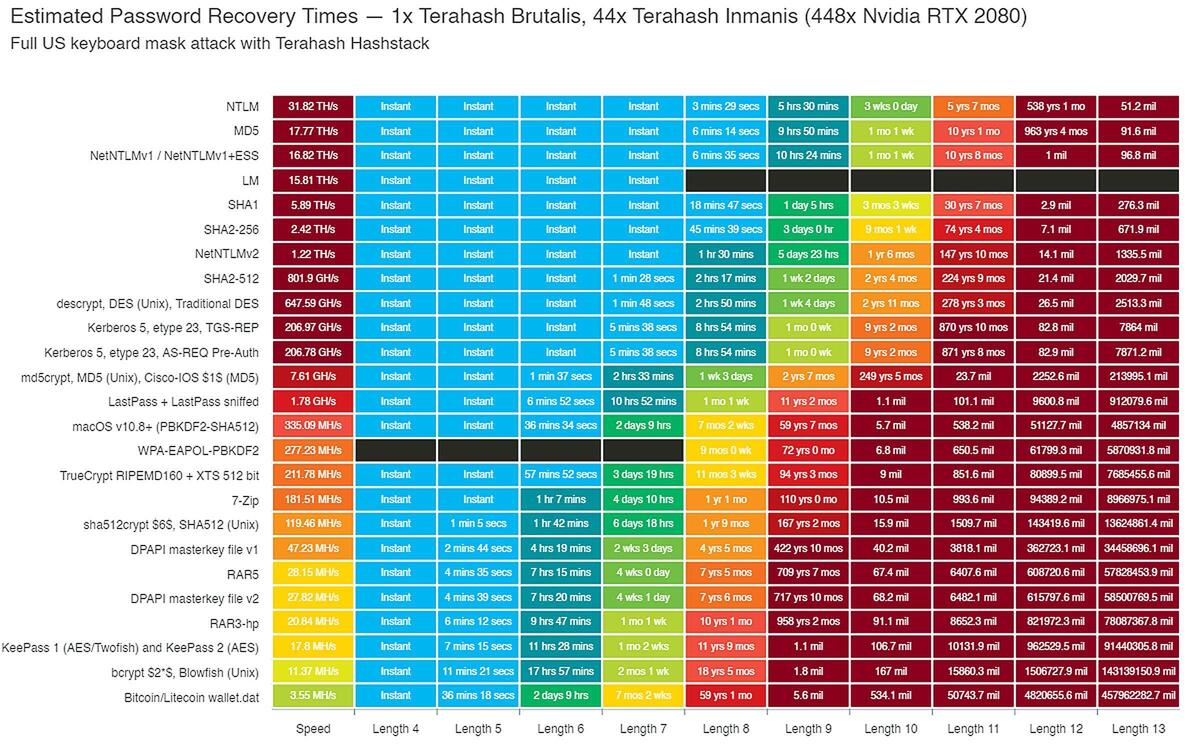 Terahash / Twitter
Terahash / Twitter Companies like Terahash can combine several hundred GPUs to create powerful password hash-cracking solutions that can break short passwords instantly. This chart illustrates how just adding a few more characters to a password can make the time necessary to crack it almost impossibly long, even with multiple GPUs.
You have some protections. Unless an attacker is looking specifically for you, a massive password breach still offers you the anonymity of being just one of many potential targets. (If a password has been associated with your username before, however, you’re much more vulnerable.)
An attacker also has to guess the entirety of your password, which is no small feat. Hackers can use dictionary attacks, trying common words and known passwords that have been breached previously. They can use masks, rules, and procedurally-generated “rainbow tables” that can make brute-force password cracking even easier.
Websites and services are (generally) on your side, however. Try entering an incorrect password on your banking site too many times—you’ll eventually be locked out and forced to authenticate with even more information. Two-factor authentication (2FA) can thwart an attacker even if they know your password. We strongly recommend that you use 2FA wherever it’s available.
Four rules for picking safer passwords
What else can you do to protect yourself? Use these rules to pick safer passwords.
Rule 1: Passwords should be as long as possible
If you do nothing else, make your passwords as long as possible. As noted above, length matters: Even a password consisting of a familiar phrase, such as JackandJillwentupthehill, is far more secure than bT6$g2 simply because the first one’s longer.
Some experts we’ve talked to say that you can stop right there. We’d still recommend making a password mildly complex, however.
Each character in a password can either be a lowercase letter, an uppercase letter, a number, or a special character like %. Using just lowercase letters offers 26 combinations per character; adding uppercase letters, numbers, and a special character can increase that to 96 combinations per character. Because password crackers can be programmed to try guesses using only lowercase characters, tossing in even a single number and special character can throw them off. That’s why banks enforce rules like picking passwords with a mix of upper- and lower-case letters, numbers, and special characters, making them a certain minimum length—and allowing you to pick even longer passwords for password managers.
Rule 2: Make unique passwords for each site or service
If one of your passwords is exposed in a breach, and matched against your username, hackers can use that information to try the same username and password on other services. That’s why it’s critical to use unique passwords, so the damage is limited to a single service.
A password manager will automatically generate unique passwords for all of the sites and services you use, solving this problem for you.
Rule 3: A password is useless if it can’t be remembered
Sure, you can ask for a password reset, but with really important passwords you risk having to go through a lengthy process of proving your identity. You either need a memorable password, or one you know where to find. (More on that later.)
What’s nice about using a password manager is that you need only one long password. If you manage multiple passwords, you’ll need to tailor them to the password length and conditions each site imposes—and that means more passwords to remember.
Unfortunately: there’s a fourth rule:
Rule 4: A password is only perfect until it isn’t
A password that’s compromised is dead to you. Once you learn of a breach, change your password as soon as you can.
Even if you haven’t been breached, if a password hasn’t been updated in several years, it could give an attacker a way to wiggle into your digital life. Don’t let them! Update passwords frequently to stay step ahead.
Six strategies for creating safer passwords
Now that you know what safe passwords require, let’s discuss some possible strategies for creating them. We’ll start with a basic password strategy, and add complexity as we go.
Strategy 1: The passphrase
For many, an excellent starting password strategy is a passphrase: some combination of words or numbers that’s long and sticks in your head. It could be a favorite saying or quotation, or a string of words that mean something to you, such as your top five ice cream flavors.
Givemeliberty,orgivemedeath!
Passphrases tend to include both capital letters and special characters. Those that include numbers add even more complexity.
Wrigley1060WAddisonSt.
One argument for not using a common passphrase by itself is that you really don’t know what a cracker has in their bag of tricks. Highly popular phrases could be used in a dictionary attack, as could passages from the Bible, for instance.
Strategy 2: Foreign languages
If an attacker uses a dictionary, they may try English phrases first. Mixing and matching languages can’t hurt, and may add complexity: Qu’est-cequec’estBigMac,otaku? gives you an idea of the possibilities.
Strategy 3: Poetry or history
If the goal is an easily memorized password, poetry is a great source of inspiration. Passages from Lewis Carroll’s poem “Jabberwocky,” for instance, or books by Dr. Seuss, contain nonsense words. Your password could be a line or two of any poem—with a slash mark between lines to add that special-character complexity. Bonus points if you haul out your copies of The Canterbury Tales or Beowulf, to add Middle-English or Old-English complexity to your passphrase.
 Mark Hachman / IDG
Mark Hachman / IDGA passphrase, a nonsense word, some capitalization—children’s books such as Oh, The Places You’ll Go by Dr. Seuss can be good sources of passphrase passwords.
Strategy 4: Don’t use anything you can find on Facebook
One of the more interesting conceptual papers on password cracking that I’ve read was this paper from Peking University’s Ding Wang and others, which looked at how just knowing some basic facts about a person—name, gender, birthday, and phone number—dramatically increased the odds that their algorithms could guess the password of a user, to the tune of a 73 percent success rate against real-world breaches. (That rate used a different, leaked password on another site and some personal information.)
The answer? Assume that what you say online on Facebook, Twitter and Instagram will be used against you.
Does that mean you can’t use your personal life as a password? Of course not. Just use information that you know, but others don’t. Don’t use names of your own family members or pets, but the names of your neighbor’s kids or pets would work.
Strategy 5: Mix it up
A 2013 password cracking study by Ars Technica revealed that “in general, capital letters come at the beginning, lower-case letters come in the middle, and symbols and numbers come at the end,” including “suffixes” of multiple random letters and numbers attached to more common words.
So mix it up. 2bornot2b,thatisthequestion doesn’t include a capital letter, but it plays with Shakespeare’s famous line a little. Just remember the end goal: A long password is the strongest password.
Security technologist Bruce Schneier has a similar, even more complex scheme, where he takes a sentence and abstracts it. “Who’s the leader of the band who’s made for you and me?” becomes “W’sTLotbW’smade4u&me?” “If you want your password to be hard to guess, you should choose something that this process will miss,” Schneier wrote.
An older strategy some may know is “l33t-speak,” where numbers can replace letters. Password crackers can be programmed for that, though, so it’s not necessarily a safe strategy anymore.
Strategy 6: The world is your password
Picking passwords that are meaningful can be as dumb as the phrase that your P.E. teacher used to greet you with, or as repetitive as the sign you see every single day announcing the freeway exit to your home.
 Mark Hachman / IDG
Mark Hachman / IDGWhether you use the covers as inspiration or the text itself, science fiction and fantasy can suggest memorable words that may be excellent passwords.
Pick a title from the bookshelf, the stranger the better. Who’s going to think of a cookbook called Twelve Months of Monastery Soups?
You can even use a book as the source of your password, then keep your password reminder in your wallet or purse. If I write “Page 69, line 2” on a scrap of paper and stick it in my wallet, an attacker needs to steal my wallet; know what the message means; know which document or book I’m referring to; have access to an identical copy to mine; and know which words I’m referring to.
Should you write down your passwords?
Writing down your passwords sounds like the stupidest thing anyone could ever do. Whether it actually is stupid depends on the situation.
Writing your passwords out in longhand, in a shared apartment with roommates you don’t necessarily trust, seems like a very bad idea. Likewise, a sticky note with your Windows password should never be left attached to the PC you use in the office.
In a home you share with family or people you trust, the argument to write down and store your passwords somewhere becomes more compelling. Storing a master password in a safe-deposit box, for example, could allow your spouse to access your online accounts in the event of your death.
A future without passwords
Passwords are becoming less important. We’re already moving toward a future where our face, fingerprint, phone, or some combination of all three provide the keys that unlock our PC, our email, and our banking site. Unfortunately, none of these alternatives are universal yet. As long as we’re still stuck with passwords, anything we can do to make them harder to crack will help keep hackers at bay.
Note: When you purchase something after clicking links in our articles, we may earn a small commission. Read our affiliate link policy for more details.
As PCWorld’s senior editor, Mark focuses on Microsoft news and chip technology, among other beats.

