Why it matters: Three vulnerabilities were recently discovered affecting uninterruptable power supplies (UPS) made by APC. The vulnerability, classified as critical and high severity, is related to APC’s SMT, SMC, SCL, SMX, SRT, and SMTL product lines. The TLS-based attacks can result in impacts ranging from physical damage of the device itself to unauthorized access to a target’s internal networks.
Device security firm Armis discovered the APC vulnerabilities. The attack vectors, collectively named TLStorm, provide hackers with the means to execute remote manipulation of the UPS. These devices supply backup power for critical devices and services in data centers, hospitals, and other organizations requiring uninterrupted backup power.
Malicious actors exploiting the vulnerability can perform remote code execution (RCE) attacks against any vulnerable APC Smart-UPS device. Such attacks enable unauthorized users to alter the UPS’s operation, potentially damaging the power supply itself or any assets connected to it. Hackers can execute the attack with no user interaction and leave no trace of a breach.
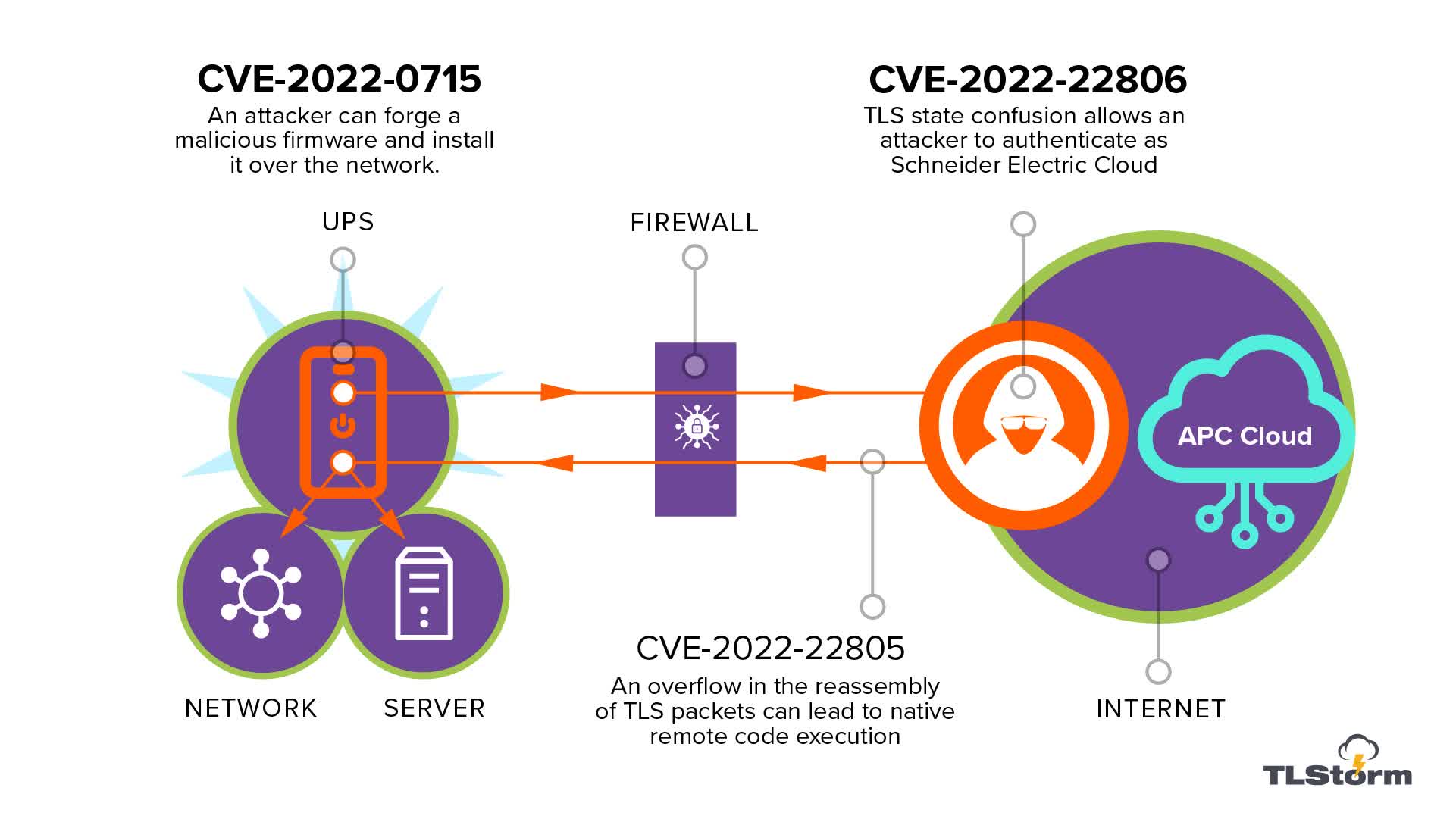
American Power Conversion’s Smart-UPS devices use a cloud connection for all configuration and control. This remote connectivity is the basis for two of TLStorm’s three vulnerabilities. The third is related to a design flaw preventing firmware updates from receiving secure cryptographic signatures.
- CVE-2022-22806 – TLS authentication bypass: a state confusion in the TLS handshake leads to authentication bypass, leading to remote code execution (RCE) using a network firmware upgrade
- CVE-2022-22805 – TLS buffer overflow: a memory corruption bug in packet reassembly (RCE)
- CVE-2022-0715 – Unsigned firmware upgrade that can be updated over the network (RCE)
Armis researchers estimate that eight out of ten companies using the devices are currently vulnerable to TLStorm-based attacks. Mitigation measures include changing the default NMC password (“apc”), installing a publicly signed SSL certificate, deploying access control lists, and installing the patches found on the Schneider Electric website.

